This is the last article about NAS series.
The scope is recapping the different technology available for NAS backup pointing in which scenario they can be adopted.
The following table has the scope of helping and discovering which VBR technology can better fit with the NAS protection service.
| Technology | v.11 and later NAS Backup | File to Tape | NDMP |
| Backup to Disk | Yes | No | No |
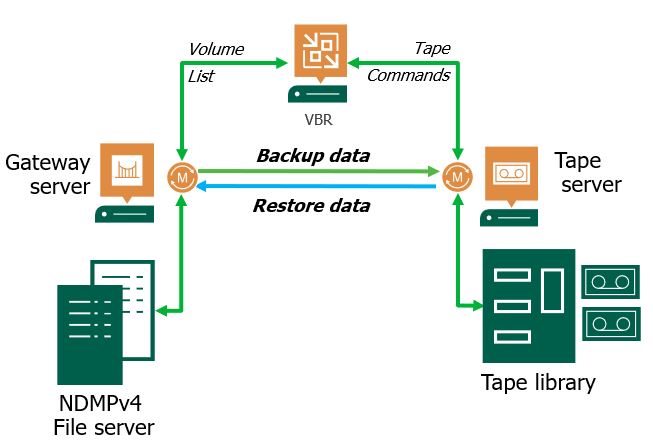
| Backup to Tape | No | Yes | Yes |
| Restore Files | Yes | Yes | No |
| Restore Entire NAS | Yes | Yes | Yes |
| Speed Backup | High | Low | Medium |
| Speed Restore | High | Low | Medium |
| Second copy | Yes to Disk | v.11 (Tape cloning) | v.11 (Tape cloning) |
| Archiving copy | Yes | No | No |
| Immutability | v.11 (Hardened Repository) | Yes | Yes |
| Object Storage | Yes | No | No |
| Scheduling | Yes | Yes | Yes |
| Licensing | VUL | Any | Enterprise Plus |
Table 1
An example:
Your managers are asking for a NAS backup architecture able to answer very astringent requests of backup and restore.
Watching table 1 and looking for the word speed it is possible to assess which VBR technology can answer the request of your managers better (in this case v.10 and later NAS backup).
Note-1: For sure the table can be improved by adding more details.
Note-2: The second tape copy and harden repository will be available with VBR v.11. Further details are available on the following web pages:
(https://community.veeam.com/blogs-and-podcasts-57/tape-improvements-in-vbr-v11-277)
Note-3: v.11 is coming soon !!! Please take a look at the launching page and register yourself: https://go.veeam.com/v11-it.
Before closing this series, I show you a hidden gem that allows extending the use of the file copy feature.
What is “File Copy” option already present on the VBR menu?
It allows to copy and move files and folders between servers and hosts added to the backup infrastructure.
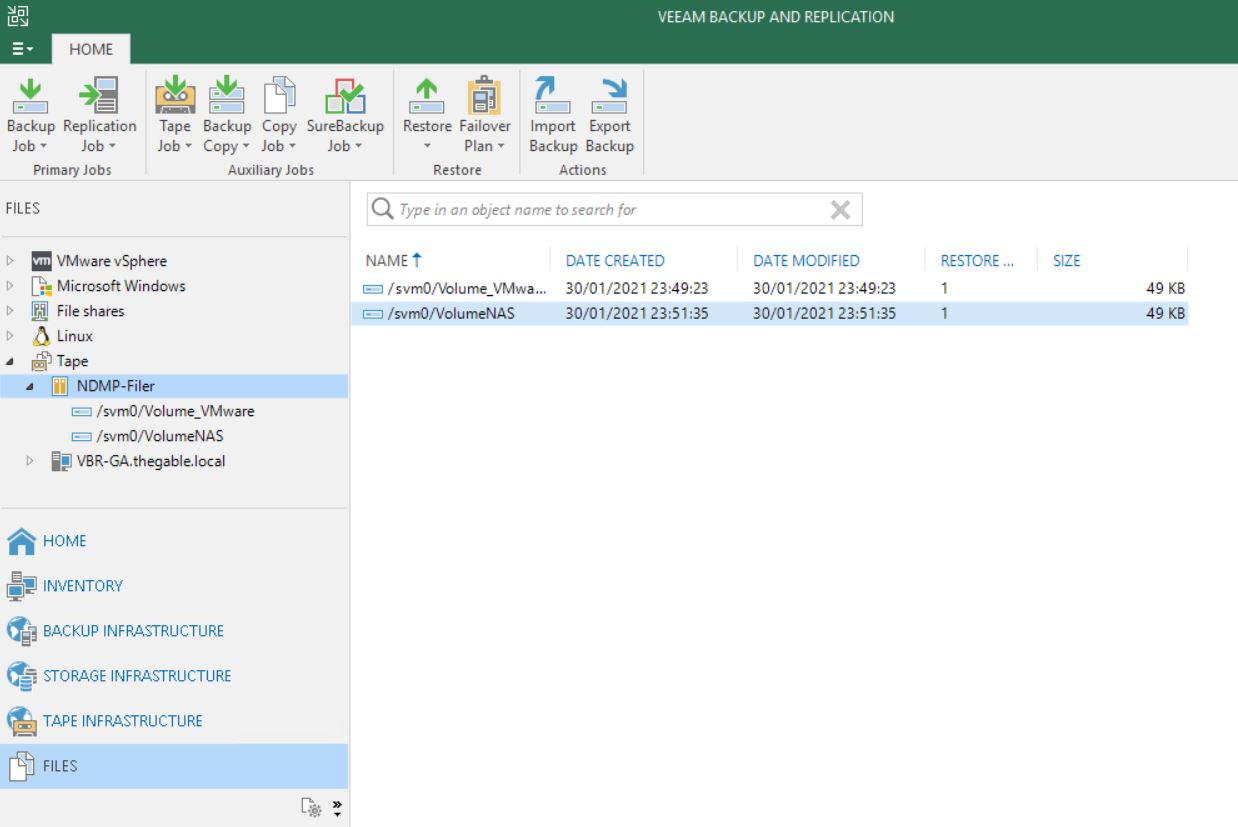
Is it possible to use it with Network share?
Not in a direct way.
Actually, No becomes a yes through the PS-tools.
What these tools are?
It is a free utility part of the Sysinternals pstools suite built by Mark Russinovich many years ago.
They allow the administrators to remotely execute commands, install software, launch applications, and run apps as the system account.
The PS-Tools package can be downloaded from the Microsoft web site:
(https://docs.microsoft.com/en-us/sysinternals/downloads/pstools)
A detailed guide is available on the following site:
https://adamtheautomator.com/psexec-ultimate-guide/
Which are the requirements?
That’s all guys. Take care

 Picture 2
Picture 2
 Picture 1
Picture 1 Picture 2
Picture 2

 Picture 1
Picture 1 Picture 2
Picture 2 Picture 3
Picture 3 Picture 4
Picture 4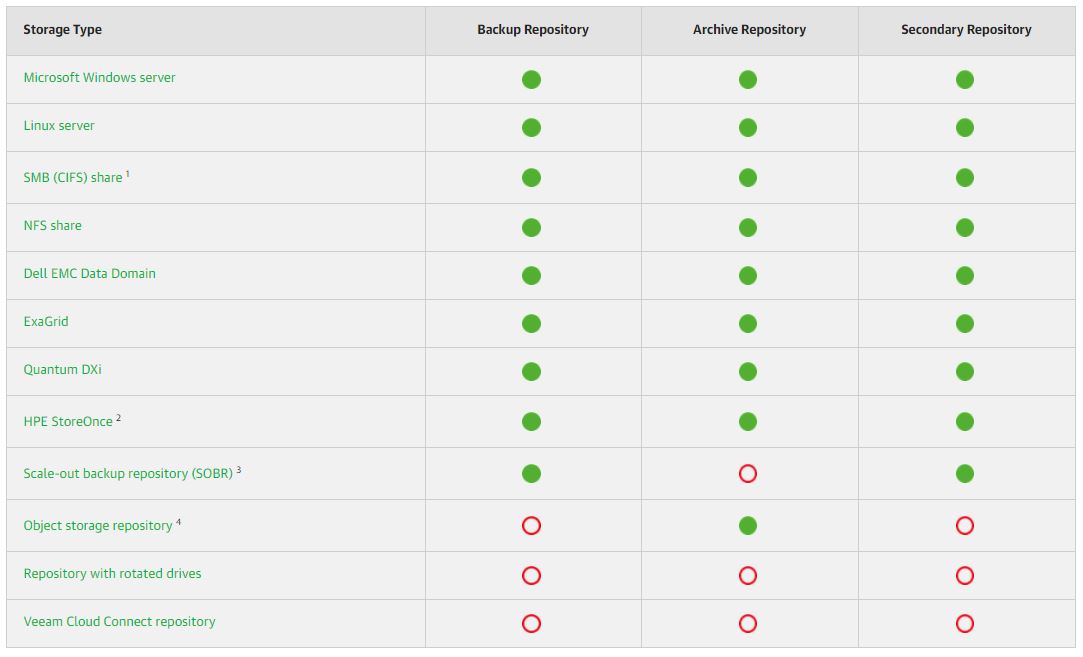 Picture 5
Picture 5
 Picture 1
Picture 1 Picture 2
Picture 2 Picture 3
Picture 3