Phase 2: Upgrading ESXi Host
In the previous article, I described how to prepare a customized ISO. If you lost it please click on this link.
Let’s continue!
Requirements: the task I performed before starting the procedure here described has been the vCenter upgrade to 7.0.1-c. I remind you that my starting point was Esxi 7.0.0.b that is fully supported by vCenter 7.0.1-c.
There are two main ways to upgrade the ESXi Hosts.
The first is related to the use of a VMware feature. It’s the vSphere Lifecycle Manager (vLCM) and you can taste part of its potential by watching this video guide.
Instead, I preferred to use an old approach working with a bootable USB pen with the custom ISO prepared in the previous article. The steps are:
1. Shutdown ESXi Hosts
2. Remove the USB-NIC
3. Insert the Pen Drive with custom ISO
4. Upgrade the host following the wizard (The main point is shown in Picture 1)
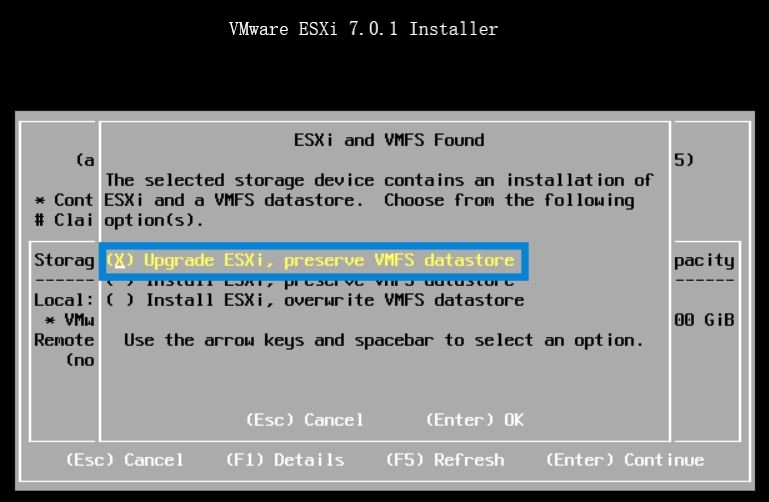 Picture 1
Picture 1
5. Reboot the host.
6. Now it’s time to install the USB-Nic Driver. It is available from “USB Network Native Driver for ESXi” web site and this article allows me to say thx to the excellent job of Songtao Zheng and William Lam
Before proceeding please read the instruction carefully and DO NOT insert all the USB cards together. (I have got three USB-NIC cards)
Why? Because during the procedure, I have had more than one purple screen and after a deep analysis I discovered that it depended on the USB-NIC cards.
To get over this issue I created the following procedure.
Picture 2
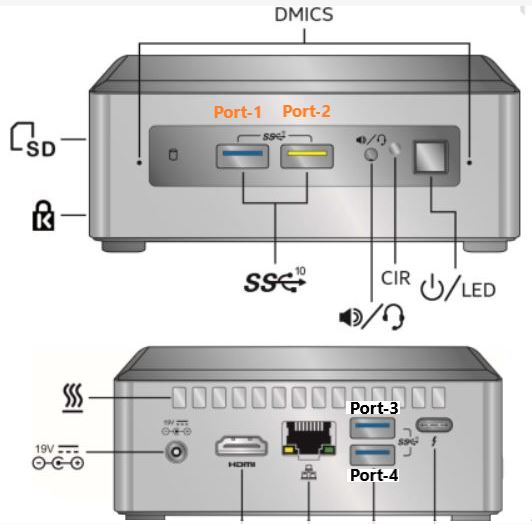
7. Switch off the ESXi NUC and insert the first USB-NIC card in port-1 and the second in port-4 (please refer to picture 2 to know the nomenclature of the port)
8. Now switch on the NUC and check if it boots correctly.
9. Switch off the NUC and insert the third USB-NUC on port-2.
10. Reboot NUC and check if it works as aspected.
Before ending this article I suggest creating a map between vmks and the physical MAC Address of the USB NIC. The main advantage is that it allows maintaining the same vmkusb address after a reboot also.
Some useful commands:
To Identify the Mac Address:
# esxcli network nic list |grep vusb |awk ‘{print $1, $8}’
To Check persisting binding:
# esxcli system module parameters list -m vmkusb_nic_fling

 Last weekend I upgraded all my Servers to the last VMware ESXi release (7.0.1 C) and this article is meant to describe all steps I performed.
Last weekend I upgraded all my Servers to the last VMware ESXi release (7.0.1 C) and this article is meant to describe all steps I performed.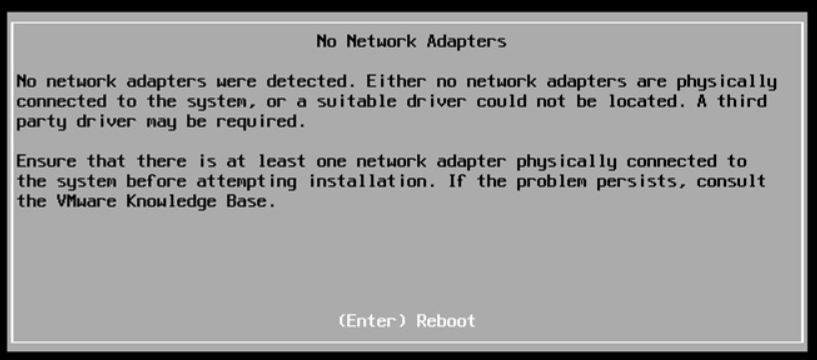 Picture 1
Picture 1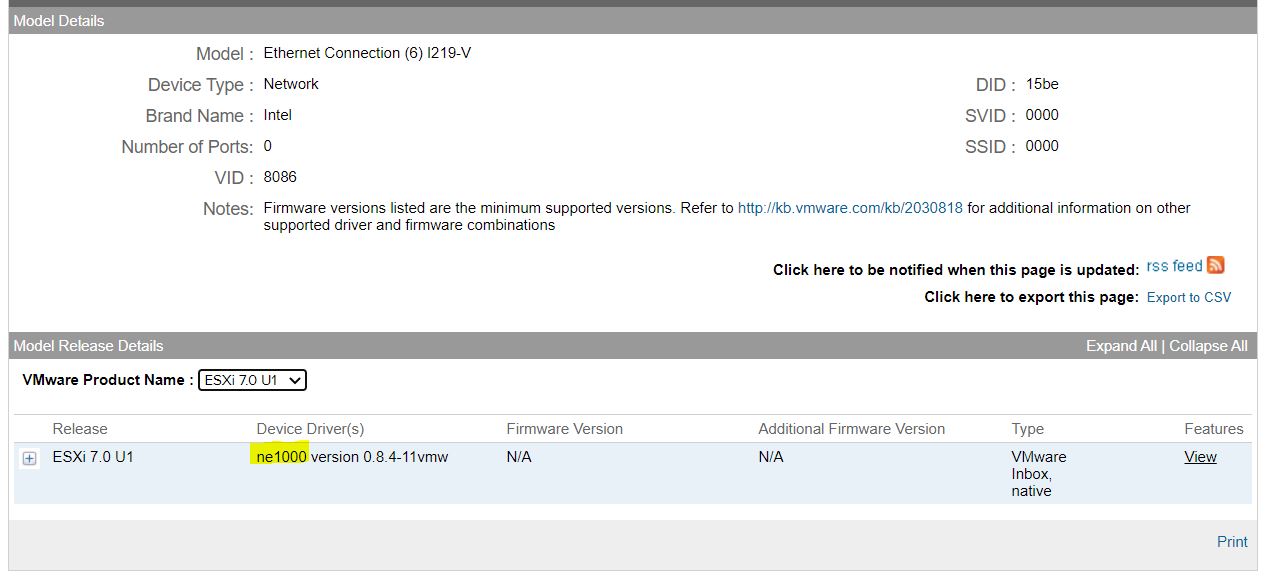 Picture 2
Picture 2