
In the previous articles, I described some good ideas to design your architecture to keep it safer as much as possible.
One of the greatest challenges the IT guys have to face is finding the right balance among design, deployment and budget.
It’s very important to have the right tools to measure architectural behaviour. In this way you can easily:
- Watch from a privileged point of view the architecture. Let’s image to be on the top of a mountain watching people and goods moving at the bottom of the valley”
- Launch the defending actions when an attack is on-going. Referring to my previous example, it’s like blocking some passages to people and goods.
- When the attack is over remove any possible threat left (cleaning the passages).
- Do a thorough workup understanding of the weak points of your architecture and create a plan to reinforce it.
Monitor tools are your sentinels, but they need to be trained to trigger also the first defense lines. Imagine the new sentinel as a lieutenant warrior with a varied arsenal of weapons.
To be clearer: the required features monitor and respond to actions in function of the severity of the alarm.
But why is measuring so important? The reason is that you can define the KPI (Key performance indicator) for your environment and periodically check if the measures are respected.
In other words, it is possible to measure the service level and understand if the budget and skill invested in the company are enough to address the backup security challenges or if more tunings actions or some great changes are needed.
Let’s see how to use Veeam One to address this common request:
The Possible ransomware activity alarm keeps tracking of the Operating system of the VM.
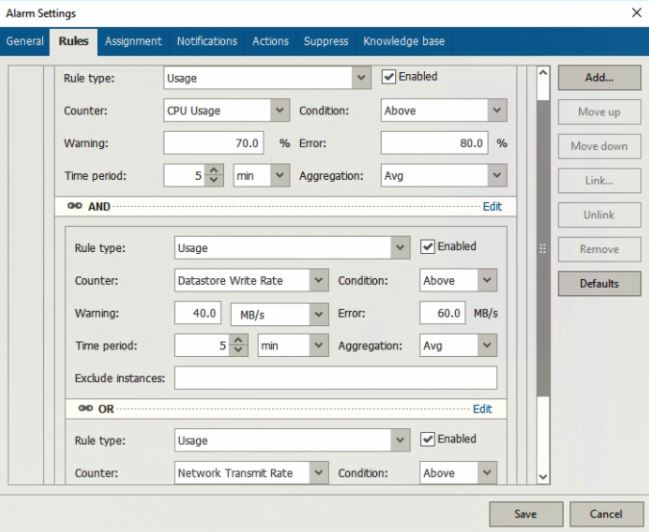
As shown in picture 1 the monitored counters are by default CPU, Datastore write Rates and networking transmit rate (the case of copy offsite of sensible data for future blackmail).
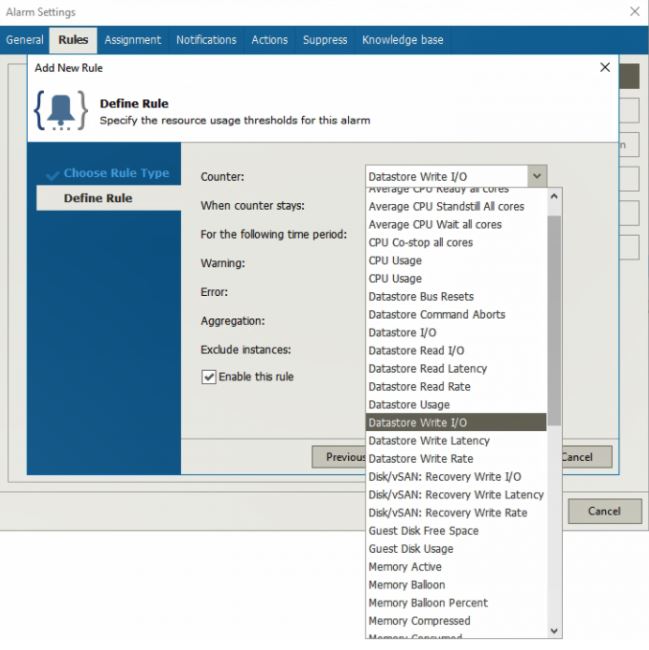
The value counters can be changed to adapt to your own needs (Tuning phases) and more counters can be added to monitor more objects as shown in picture 2.
 Picture 1
Picture 1
 Picture 2
Picture 2
Another alarm already present in Veeam One is “Suspicious increment backup size“.
It checks if the restore point size is significantly different from the previously created ones.
The two main reasons I like Veeam ONE are:
- Very easy to use
- Customizing the action after an alarm has been triggered
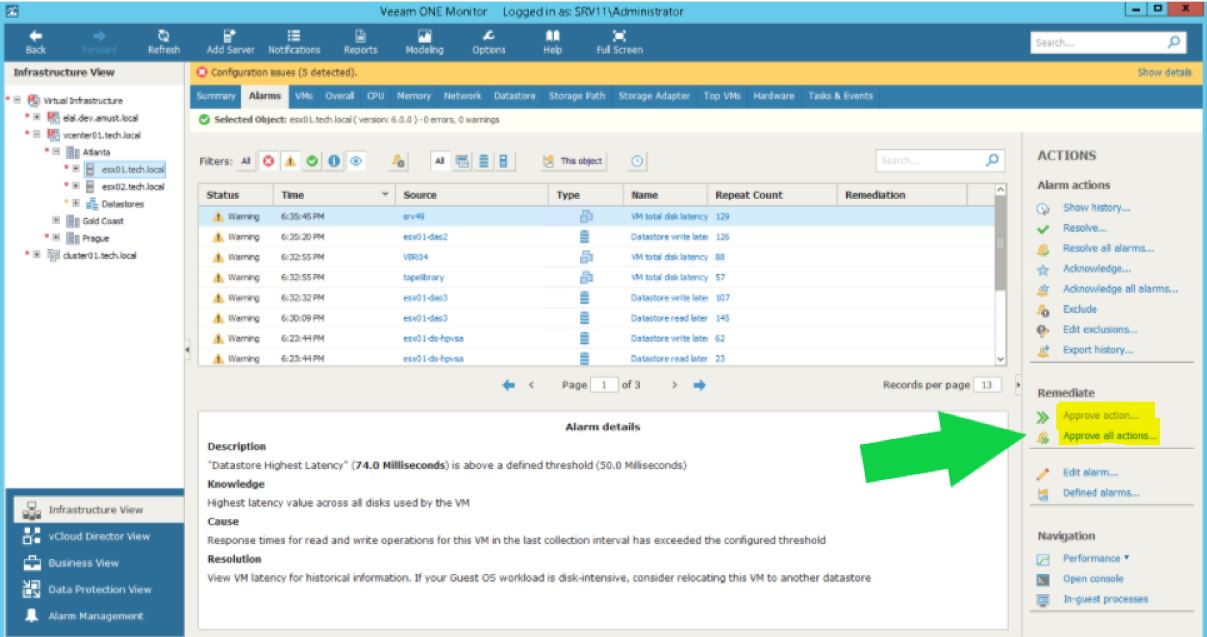
Thx to “customizing action” it’s possible to launch your antivirus/antimalware on the VMs belonging to the backup job that has triggered the suspicious alarm, or disconnect the repository from the network, or what else you wrote on your incident and rescue procedure.
The main point here is that you can manually click on it or automatically execute the action as shown in picture 3
 Picture 3
Picture 3
Veeam One has furthermore an exhaustive technology of reporting.
If an alarm is a good way to intercept an error or a misconfiguration because it works in real-time, through the reporting it is possible to check the status of your protection (KPI, SLA….), understanding the exercise and security cost of your production environment and forecasting the new investment to implement in the next years.
Which are the reports to use?
All of them are important and an all report list is available from the following link: Reports
Just as an example please check the use of the following
- Verified VM (SureBackup)
- Protect VM (Protected means a valid backup in a specific RPO)
- Backup Billing (chargeback capabilities)
- Infrastructure charging
- Repository Capacity planning
- Infrastructure change Audit
The next article will talk about which are the automatic procedures you can adopt to check your backup infrastructure.
Take care and see you soon
